KEY TAKEAWAYS:
--Seven factors are highly predictive of vulnerability to a breach.
--They can be measured precisely, using questions that go far deeper than the standard Yes/No questions like, "Do you have a software patching cadence in place?"
--The seven factors can be monitored continuously, providing an up-to-date understanding both to the insurer and to the client.
----------
Cyber insurance policy application forms are the equivalent of a dating profile. You don’t really know if the person’s picture is up to date, or if what they’re saying about how much they drink and what they do for a living is true. And the cyber applicant isn't necessarily even being deceptive. The person who filled out the profile may not have an accurate understanding of themselves, so how could they give you the complete picture?
For cyber insurance companies to provide optimal quotes and manage their risk exposure, they need a comprehensive and predictive view of risk -- and it needs to be the same view that policyholders have.
Questionnaires about insureds’ cyber hygiene and honor system-based notice of circumstance declarations are insufficient. Enter security ratings. As attack surfaces grow, as the number of connected devices increases and as breaches become more prevalent, this continuous, external scanning provides an always-updated view of risk—both of an organization and of its third and fourth parties.
By mapping out digital assets, observing events and settings on these assets and correlating them to cyber incidents, SecurityScorecard assigns an A-F rating and a score of 1-100. Ratings are entirely evidence-based, scored on an underlying and transparent observation from scans of the entire IPv4 space.
Win-win cyber risk management for insurance providers and policyholders
Together, Marsh McLennan Global Cyber Risk Analytics Center and SecurityScorecard studied how cybersecurity ratings can help insurance companies provide quotes and manage their risk exposure while also offering customers the opportunity to improve their security posture.
We found seven factors that are most predictive of a breach. They are:
- Endpoint Security: Looks at the security of an organization’s operating systems, web browsers and related active plugins
- Patching Cadence: Analyzes how quickly an organization installs security updates
- Ransomware Score: Measures how susceptible the organization is to a ransomware attack
- Network Security: Checks public datasets for evidence of high-risk or insecure open ports within the organization’s network
- DNS Health: Measures the health and configuration of an organization’s DNS settings.
- IP Reputation: Uses the SecurityScorecard data, open-source malware information and third-party cyber threat intelligence data-sharing partnerships to assess the reputation of an organization’s IP addresses
- Cubit Score: Measures a variety of security issues that an organization might have to identify whether it is adhering to best practices
Taking the steps to mitigate risk associated with these factors will significantly strengthen an organization’s security.
See also: Why Cyber Strategies Need Personalization
How predictive are the seven factors of cyber risk?
Let’s get nerdy. To discover which factors are statistically significant, we combined incident data from Marsh McLennan with SecurityScorecard’s ratings data, dating back to 2018. We enriched the incident data with firmographic data including North American Industry Classification System (NAICS) industry codes and company revenue. The joint data sets gave us approximately 12,000 unique, globally distributed entities covering a range of revenues and industries.
The chart below shows the 95% “confidence interval”—meaning that there’s a 95% probability that the results will fall within these parameters—of the “correlation coefficient,” the statistical relationship between two variables, for all of the entities in the study.
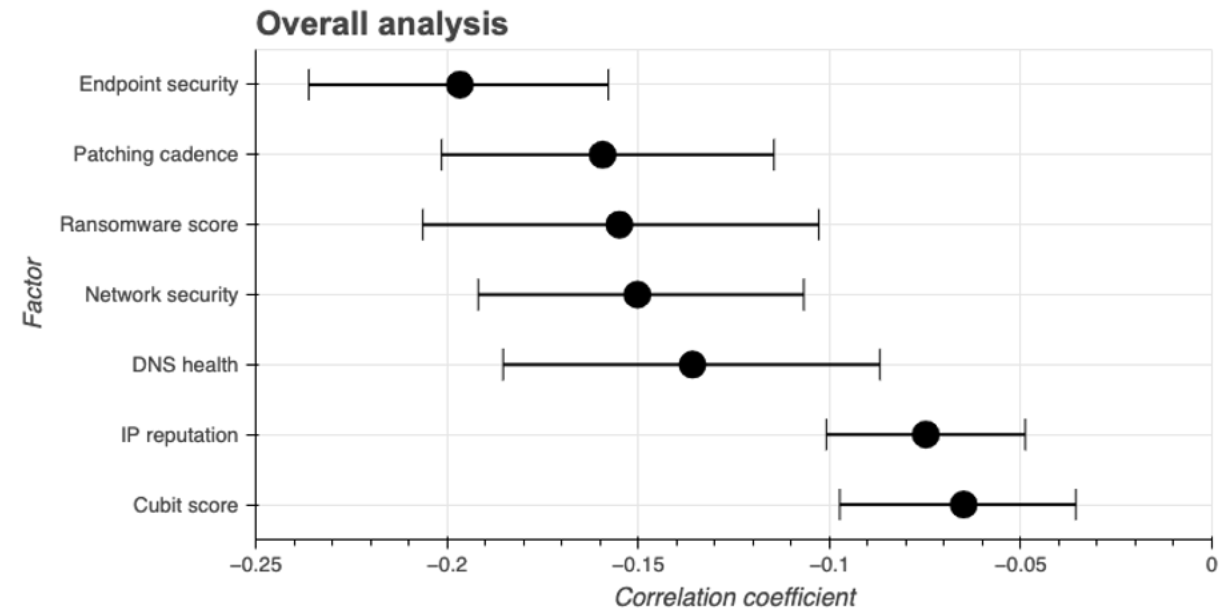
Keeping in mind that a correlation of -1 indicates perfect correlation, these results suggest that the seven factors have strong predictive power.
As you can see, endpoint security is the strongest predictor of a cyber incident overall. [The Cybersecurity Infrastructure and Security Agency (CISA) recognizes the importance of endpoint security, as well. They issued an alert that identified common exploitation vectors and recommendations for mitigation.]
See also: Cybersecurity Trends in 2023
Security ratings boost cyber resilience
The need for cyber insurance is growing, yet only 55% of organizations have policies. And even though enterprises spend a mean of $2.4 million to find and recover from a breach, only 20% have coverage of more than $600,000.
It behooves both cyber insurers and their policyholders to take the steps necessary to improve cyber resilience.
In addition to providing a way to quantify and assess risk, security ratings allow providers to stop asking simple questions that require complex answers. Rather than asking a binary "Yes or No" question like, “Do you have a software patching cadence in place,” they’re able to answer complex questions like, “Do you have any high-severity CVEs in your environment, and if so, how long have they remained unpatched?” This is the level of detail required to underwrite cyber risk in the 21st century, and it’s why security ratings are becoming a bigger part of insurers’ profitable growth strategies.
Security ratings and data offer a transparent, two-sided view that reduces information asymmetry so that all interested parties can better understand and measure cyber risk.
And being aware of the seven factors most predictive of breaches can inform underwriting strategies and help the industry move toward a more sustainable future. A historical view over at least a year is also important, because most cyber policies are written on a claims-made basis. A data breach or other cyber compromise can take many months to come to light, and it’s smart to avoid underwriting an organization in the midst of one.
Using ratings in underwriting strategies supports insurance companies to more accurately evaluate cyber risk exposure and inform risk selection decisions. Knowing which way to swipe, as it were, drives an efficient risk transfer market with all interested parties on the same page. This helps make all of us—and the world—safer.






